ELECTRONIC WARFARE
Military Electronic Warfare
Electronic Warfare on Civilians
Electronic warfare includes several basic principles that apply to military use and warfare on civilian alike:
1. Electronic Support (ES): Includes the ability to detect and analyze the enemy’s electronic emissions. This includes detecting the enemy’s communication systems and radars.
2. Electronic Assault (EA): This is intended to disable or mislead the enemy’s electronic systems. For example, blocking or spoofing radio signals.
3. Electronic Countermeasure (ECM): The ECM provides protection against electronic attacks from the enemy. This includes defensive measures against enemy signal blocking or deception attempts.
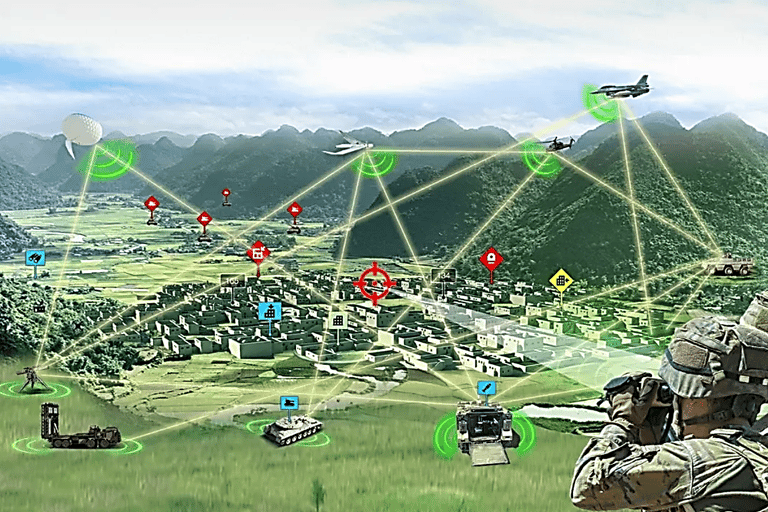
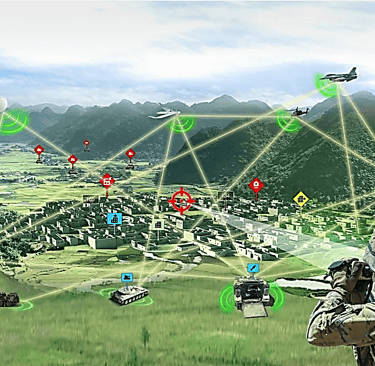
All military equipment, drones, planes, helicopters, tanks, have microwave and laser technology to break the enemy or kill them.
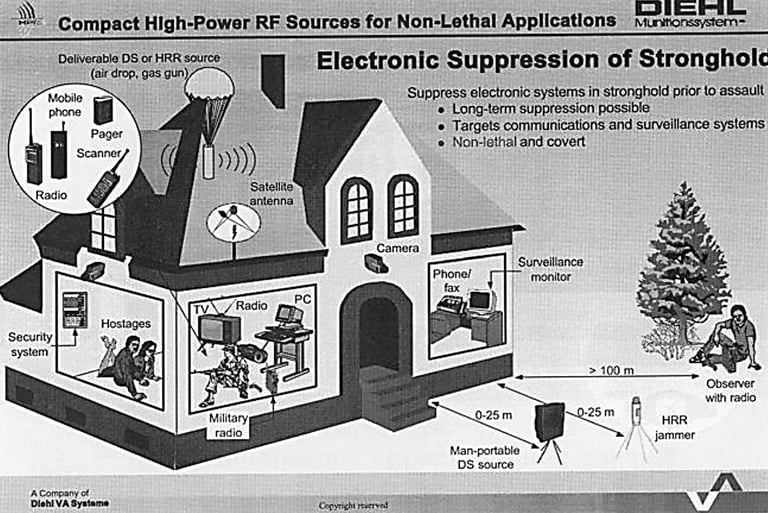
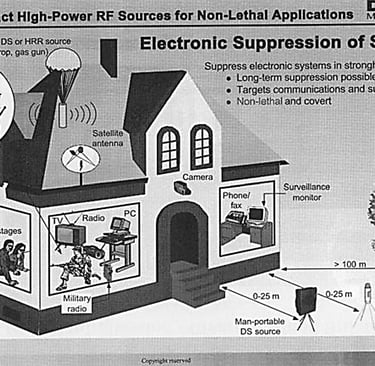
All military equipment is being adpted to use on men, women and children. It has microwave and laser technology to break the civilian enemy or kill them.

The US has the ultimate in electronic warfare equipment to suppress, harass and destroy...
...the civilian fights a lone fight with personal phones and computers in their homes and cars.
Remember, civilians are not the aggressors and they have no defense against military actions. Military strategy and tools are being used against US citizens and other Targeted Individuals across the world.
Electronic Warfare08 February 2012
https://info.publicintelligence.net/JCS-EW.pdf
"5. Electronic Warfare Capabilities and Potential Effects
a. EW is conducted to secure and maintain freedom of action in the EMOE [Electronic Operating Environment] for friendly forces to deny the same to the adversary. As an adaptive and responsive form of disruptive or destructive fires, EA’s purpose is to gain and maintain friendly advantage within the EMOE and ensure requisite friendly access to the EMS. EW can be applied from all physical domains by manned and unmanned systems. EW may adversely affect friendly forces when not properly integrated and coordinated. EW is employed to create decisive, standalone effects, or to support military operations by generating various levels of control, detection, denial, deception, disruption, degradation, exploitation, protection, and destruction. EW can further affect the OE by influencing both friendly and adversary leaders and population. EW plays a role at the tactical, operational, and strategic levels of war. Performing EA against an early warning radar, for example, has effects at all levels of war. Tactically, it affects cueing of engagement systems. Operationally, it affects the adversary’s ability to mass and synchronize forces. Strategically, it prevents the adversary’s senior leadership from maintaining a coherent picture of the national security environment. In another scenario, operational remediation of EMI against a national space-based asset (an EP-related process) would call for direction finding (DF) and geolocation of the source (through ES), and perhaps the decision to conduct EA on that source if attributed to hostile intent. While the actions described in this scenario occur within a tactical, time-sensitive context, the ramifications of the events could have strategic or operational-level significance. The value of EW is manifested fully only when commanders consider and employ capabilities across the OE.
b. EW is vital throughout all phases (shape, deter, seize initiative, dominate, stabilize, and enable civil authority) of an operation or campaign. EP attributes and processes are essential across all phases of conflict to ensure all EMS-dependent capabilities are able to operate effectively in operationally stressed EMOEs. During the shape and deter phases, ES assets contribute to the overall understanding of the OE. A judicious commander may employ EW to implement favorable intelligence preparation of the OE without prematurely crossing the threshold to conflict. The potential to employ nondestructive and nonlethal capabilities make EW assets vital to the preparation of the OE. Using EW, joint forces may set the conditions for combat when imminent and prosecute the attack once combat is under way. The ability to achieve an objective through nondestructive means may allow a more rapid transition from the seize initiative and dominate phases to support operations in the stabilize phase. EW may also employ destructive EM fires, decisive for achieving campaign objectives during the seize initiative and dominate phases. From the stabilize to enable civil authority phase, EW can foster restorative operations by offering nonlethal options such as force protection through ES to monitor subversive elements; EP for ensuring communications capabilities continue to function in EMOEs; EA to counter radio-controlled improvised explosive devices; or broadcasting selected themes and messages, to include civil defense messages, to assist civil authorities.
c. EW applications in support of homeland defense are vital to deter, detect, prevent, and defeat external threats such as ballistic missiles, aircraft (manned and unmanned), maritime vessels, land threats, hostile space systems, domestic/international terrorism, and cyberspace threats.
d. When used in support of a deterrence activity or operation, the role of EW goes beyond simply being available to support potential combat operations. EW can support the shaping of adversaries’ perceptions and morale, as well as unit cohesion. EW applied toward deterrence objectives can sever lines of communications, logistics, C2, and other key functions while simultaneously protecting friendly capabilities. The physical presence of EW assets (e.g., airborne ES platforms), as well as enabling freedom of navigation activities, can reinforce the deterrent message.
e. Control. The overall goal of EW involves the use of EM energy and DE to control the EMS or to attack the enemy. Control of the EMS is achieved by effective management, coordination, and integration of friendly EMS-dependent systems (e.g., communications, ISR, EW, computer networks) while countering and exploiting adversary systems. EA limits adversary use of the EMS; EP secures use of the EMS for friendly forces; and ES enables the commanders to identify and monitor actions in the EMS throughout the OA. EMBM provides the enabling JEMSO processes to ensure effective control of the EMOE. Additionally, commanders should maximize integration among EW and their other combat capabilities as part of their combined arms operations. Activities in control of the EMS can include, but are not limited to:
(1) Detection. Detection is identification of potential enemy EM emissions through use of ES measures. It is the essential first step in any follow-on EW activity. Friendly forces must have the capability to detect and characterize interference as hostile jamming or unintentional EMI.
(2) Exploitation. Exploitation is taking full advantage of any information that has come to hand for tactical, operational, or strategic purposes. In an EW context, exploitation is ES that refers to taking full advantage of adversary radiated EM energy to identify, recognize, characterize, locate, and track EM radiation sources to support current and future operations. Data transmissions produce EM energy for exploitation by SIGINT, provide targeting for EM or destructive attacks, and develop awareness of operational trends.
Examples of exploitation include geolocation of terrestrial EMI sources impacting space assets, terminal homing on adversary communication devices, determination of enemy indications and warnings, and geolocation of RF apertures in cyberspace for targeting. Exploitation may be enhanced or enabled by EA to stimulate target EMS-dependent systems.
(3) Denial. Denial is defined as the prevention of access to or use of systems or services. This can be accomplished through numerous means (e.g., EW, computer network operations [CNO], destruction, etc.). Denial, in an EW context, is the prevention of an adversary from using EMS-dependent systems (e.g., communications equipment, radar) by affecting a particular portion of the EMS in a specific geographical area for a specific period of time. Denial prevents an adversary from acquiring accurate information about friendly forces. Denial is accomplished through EA techniques (degradation, disruption, or deception); expendable countermeasures; destructive measures; network applications; tactics, techniques, and procedures (TTP); and/or EMCON.
(4) Disruption. Disruption is to interrupt the operation of adversary EMS-dependent systems. The techniques interfere with the adversary’s use of the EMS to limit the adversary’s combat capabilities. A trained adversary operator may be able to thwart disruption through effective EP actions such as changing frequency, EM shielding, etc. The goal of disruption is to confuse or delay adversary action. Disruption is achieved with EM jamming, EM deception, and EM intrusion. These enhance attacks on hostile forces and act as force multipliers by increasing adversary uncertainty while reducing uncertainty for friendly forces. Advanced EA techniques offer the opportunity to nondestructively disrupt or degrade adversary infrastructure.
(5) Degradation. Degradation is to reduce the effectiveness or efficiency of adversary EMS-dependent systems. Degradation may confuse or delay the actions of an adversary, but a proficient operator may be able to work around the effects. Degradation is achieved with EM jamming, EM deception, and EM intrusion. Degradation may be the best choice to stimulate the adversary to determine the adversary’s response or for EA conditioning.
(6) Deception. Deception is measures designed to mislead the adversary by manipulation, distortion, or falsification of evidence to induce the adversary to react in a manner prejudicial to the adversary’s interests. Deception in an EW context presents adversary operators and higher-level processing functions with erroneous inputs, either directly through the sensors themselves or through EMS-based networks such as voice communications or data links. Through use of the EMS, EW manipulates the adversary’s decision loop, making it difficult to establish an accurate perception of objective reality.
(7) Destruction. Destruction is to make the condition of a target so damaged that it can neither function as intended nor be restored to a usable condition. When used in the EW context, destruction is the use of EA to eliminate targeted adversary personnel, facilities, or equipment. Sensors and C2 nodes are lucrative targets because their destruction strongly influences the adversary’s perceptions and ability to coordinate actions. Space assets on orbit, as well as computer services in cyberspace, are potentially lucrative targets as well. EW, through ES, supports destruction by providing actionable target locations and/or information. While destruction of adversary equipment is an effective means to permanently eliminate aspects of an adversary’s capability, the duration of the effect on operations will depend on the adversary’s ability to reconstitute.
(8) Protection. Protection is the preservation of the effectiveness and survivability of mission-related military and nonmilitary personnel, equipment, facilities, information, and infrastructure deployed or located within or outside the boundaries of a given OA. It involves the use of physical properties, operational TTP, as well as planning and employment processes to ensure friendly use of the EMS. This includes ensuring that EW activities do not electromagnetically destroy or degrade friendly intelligence sensors, ccommunications systems, PNT capabilities, and other EMS-dependent systems and capabilities. Protection is achieved by component hardening, EMCON, EMS management and deconfliction, and other means to counterattack and defeat adversary attempts to control the EMS. Spectrum management and EW work collaboratively to accomplish active EMS deconfliction, which includes the capabilities to detect, characterize, geolocate, and mitigate EMI that affects operations. Additionally, structures such as a joint force commander’s electronic warfare staff (JCEWS) or electronic warfare cell (EWC) enhance operational-level EP through coordination and integration of EW into the overall scheme of maneuver. It is not always possible to prevent the degradation of friendly systems from the effects of friendly forces’ EW operations. In these cases, the JFC should make a determination on which system has a higher priority based on the capability provided by each system."
Principles Applied Against TI's
Deny freedom of action. Applied that means interference in their job, house, travel, shopping, family, everything.
Contact employer, doctor, stores, restaurants and enlist involvement in these wrongful and criminal acts.
Contol the support system to degrade and destroy the TI.
Control the media and population to believe TI is mentally unstable, delusional so their testimony re the coherent picture of their torture is not believable.
Targeted Individuals are living in a very complex environment. An aggressor has taken over their homes and their bodies. Military strategy has been adapted for use in a civilian context against targeted people who have no defense.
The "group" has been built and defined by putting people on a list. It is as if they were an ethnic race which is set to be eliminated. It is an extremely unfair attack and the criminal actors need to be exposed. The concepts of war are exactly the same, except they are carried out on ordinary doctors, nurses, scientists, artists, teachers, students, truck drivers, mothers, and children. This must be kept under wraps so that it can go on. DENIAL and DEGRADATION are the operators. Targeted Individuals continue to suffer. They are separated and segregated and isolated to render them even more helpless.
It is yet another massacre by government aggressors. The Nazies kept the concentration camps secret for at least 9 years before the holocaust became known. News reports were published in newspapers, including the New York Times, in late 1942. However, the sheer scale and horror of the events made them seem unbelievable or exaggerated to many in the general public, and the news was often downplayed by officials and media outlets. The public did not fully grasp the extent of the atrocities until the concentration and extermination camps were liberated by Allied forces at the end of the war in 1945. The same is happening today to Targeted Individuals. The media downplays the atrocities taking place upon them.
Targeted Individuals have been made a group by their similar experiences. They are not self-defined. They have been defined by the persons who made the lists. Do you remember what Hitler did to the Jews and other groups. The World Has Forgotten!
The Stages of Genocide
https://www.theholocaustexplained.org/what-was-the-holocaust/what-was-genocide/eight-stages-of-genocide/
In 1987, Gregory Stanton, a professor of law, published a paper which explored how genocides develop and unfold.
In his original work, Stanton identified eight key stages which resulted in acts of genocide. According to Stanton’s model, some of these stages can happen at the same time or in a different order. In 2012, Stanton expanded on these ideas, and added two further stages (Discrimination and Persecution) to make ten. According to Stanton’s current model, therefore, the stages of genocide are as follows:
Classification – Dividing people into ‘them’ and ‘us’.
Symbolisation – Forcing groups to wear or be associated with symbols which identify them as different.
Discrimination – Excluding groups from participating in civil society, such as by excluding them from voting or certain places. In Nazi Germany, for example, Jews were not allowed to sit on certain park benches.
Dehumanisation – To deny the humanity of one group, and associate them with animals or diseases in order to belittle them.
Organisation – Training police or army units and providing them with weapons and knowledge in order to persecute a group.
Polarisation – Using propaganda to polarise society, create distance and exclude a group.
Preparation – Planning of mass murder and identifying specific victims.
Persecution – Incarcerating groups in ghettos or concentration camps, forcibly displacing groups, expropriating property, belongings or wealth.
Extermination – Committing mass murder.
Denial – Denial of any crimes. This does not necessarily mean denying that the acts of murder happened, but denying that these acts were a crime, and were in fact justified.
Stanton hoped that by identifying these stages it would be easier to recognise genocide before it took place and thus stop it from happening.


Join us in advocating against harmful technology misuse.
contact@targetedhumans.org
© 2025. All rights reserved.
Targeted Humans Inc.